Digital evidence has become more and more relevant for most civil and criminal investigations. Developing your OSINT skills is ongoing and understanding where it is all headed is just as important. It is an ever changing area, with new social media platforms sprouting up all the time.
When conducting online research on a person of interest for your investigation, it is important to develop a solid strategy. Once you begin gathering information, a clear chain of custody must be obtained with anything you find online. Additionally, authentication of social media posts or profiles are becoming more and more important to a case.
“We need all videos extracted and the subject’s social media profile captured and preserved.”
Recent client request
We are getting more and more requests like this every week. When a suspect or person of interest gets legal council, they may be advised to delete all their social media. That is why time is so important and it is becoming more important to start with online investigations before you do anything else. Many attorneys and PI’s have learned the hard way that what is here today, may be gone tomorrow. Understanding the differences in digital evidence can set your Private Investigation firm apart from the others.
The purpose of this blog post it to explain some of the differences in the capture of online evidence.
Screenshot Digital Evidence
Most of the time your OSINT discovery process is centered around a specific strategy and focus. The gathering of online information, its chain of custody, and your final report can and should contain screenshots and corresponding URLS. However, what if the Instagram post or video is just the digital evidence you were looking for? What if you know your attorney client is going to need this in the deposition, civil or even criminal case? It is times like this where a screenshot is not enough. Taking that extra step can be very valuable.
Social Media posts may not only be deleted or turned off, but they can also be edited. The post you see today may not be the same post you saw during your online investigation. Unless you have preserved the original post, you may not be ale to prove what was originally said.
For social media and web page evidence to be valid and accepted according to the Federal Rules of Evidence:
Original source code of the social media message, blog or webpage must be collected
Metadata must be collected
Digital signatures and timestamps must be placed on the data to provide evidence of data integrity & authenticity
Data should be prepared in EDRM-XML for easy processing & analysis in eDiscovery systems
Preserving the Digital Evidence
*Establishing a valid chain of custody means being able to show where the evidence has been, who has handled, and its condition at all times, in order to establish that there has been no alteration or tampering of the evidence prior to the time it is presented to the court. With respect to web pages and social media accounts, then, this means that the party propounding the evidence must establish:
- When the record was originally produced;
- That the record is an accurate recording of the webpage in question;
- That the record was not subject to alteration from the time it was collected until the time it is presented in court.
Using the correct tool instantly generates a forensic report using a forensic SHA256 hash, and HTML source code. It means that your online preservations contain key identifying Metadata such as the timestamp, the URL, the IP address, the date, and the time of capture, using a certified Stratum-1 atomic clock in compliance with the eSign Act.
As a result, you can capture the evidence you need at the moment you need it, with the assurance that when you do, you are collecting evidence which contains the necessary hallmarks of authenticity that courts are increasingly seeking.
(*Web Preserver), This is the software we use at eChatter when we need to preserve digital evidence for our clients.
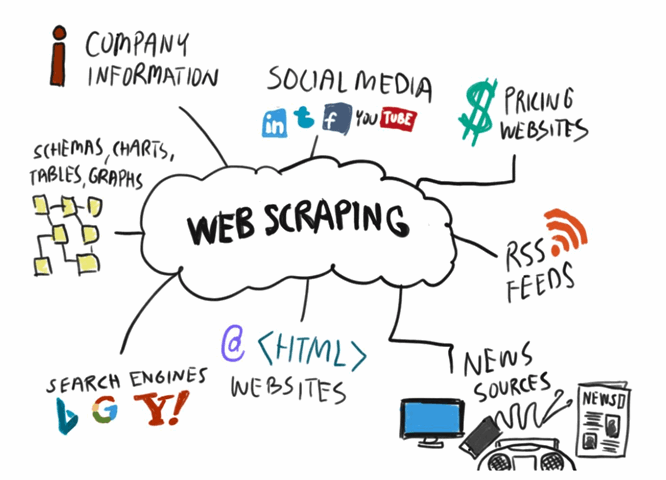
Web Scrapping
Can a website be scrapped or archived? Yes and It may surprise you to know just how often it is used. Web archiving tends to concentrate more on the look and feel of a website or profile. The Wayback Machine (a.k.a. archive.org), is designed for web archiving. They explain their company this way, “The Internet Archive, a 501(c)(3) non-profit, is building a digital library of Internet sites and other cultural artifacts in digital form.” It is like an online library of websites. ( As an aside, it is also a great way to check if a person of interest worked for a certain business years ago, as they may have been featured on the website).
Web scrapping is more focused on textual data. The most crucial step for initiating a web scraping project is to select a tool to fit your research needs. There a tons of them out there to choose from. It is important to remember that the collection of data, while publicly available, is still a collection produced by others. Depending on the case, be aware of the potential privacy and security implications and proceed with caution.
Web scrapping can be used for price monitoring, lead generation, marketing and research. The complexity of many websites makes it difficult to scrape data unless you know code. Software applications make this task easy for anyone and is not dependent on skills.
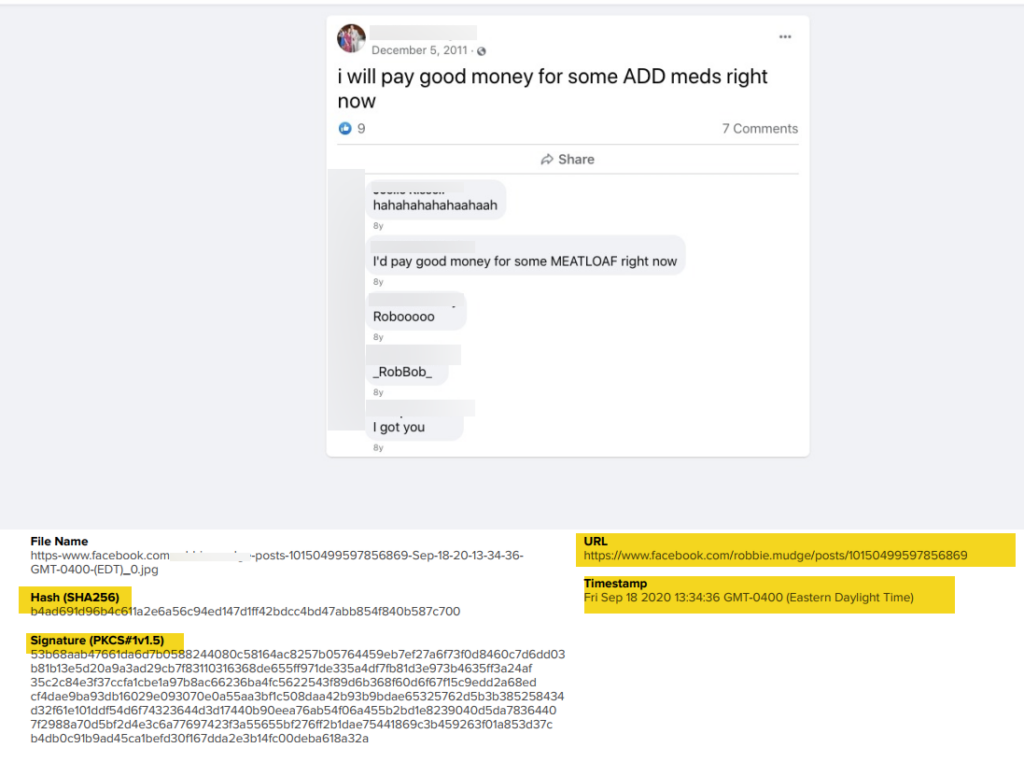
Example of a Preserved Post
The post below is a great example of what is captured during the preservation of a post. The key components are the URL, Timestamp (when the post was discovered), Hash, and Signature.
An entire profile of a person of interest can be over 100 pages and is captured in PDF report format.
By: Kathy Doering.
Kathy is President of eChatter, and is McAfee certified in OSINT and is a certified Social Media Intelligence Analyst (SMIA). Kathy also serves as president of The Global Social Media Research Association.