We get this question a lot. Can you tell me where this social media photo was taken? The short answer is probably not. Here’s why~
An easy way to explain this is to think of the chain of custody of a photo. How was the photo taken originally? Chances are, it was taken using a person’s smartphone. It could, in some cases, have been taken using a digital camera.
Digital cameras can store a lot of relevant information about a photo. It can reveal where it was taken, how it was taken & when it was taken. Digital Forensic Investigators and Examiners know exactly how to extract this data from a photo & use it to fight child exploitation and sexual abuse.
However, what many people don’t know, is that the data behind the photo can be manipulated and changed.
Geotagging a Post or Photo
It was once very popular to post a photo in social media and tag the photo by letting everyone know where you are. Remember Four Square? Many people still do this. You may see a friend who posts a photo on a beach and they tag who they are with and where they are. Those are the easy ones!
However, many people have learned the hard way not to do this. Not only does a geotag let criminals know where you are, they also let them know you aren’t home. Most people are very well aware of their privacy settings on their mobile phone and in social media.
Therefore, it is near impossible to determine where a social media photo was taken, if the geotag is set to private or is off altogether.
So what is the data behind the image? It is called EXIF data.
EXIF Data
What is EXIF data? EXIF stands for Exchangeable Image File Format. It is basically the metadata attached to every digital photo you take. It will include information such as the camera model and settings you used, the date and time you took the picture, and even details about exactly where you took the picture. Photographers can use this data to help organize their photos, perform searches, or re-create the exact manner in which a picture was taken.
** But – please note: Facebook and other social media platforms do not publicly share EXIF Data. They strip it when it is uploaded.
The FBI warns against sending photos through the internet or sharing on some social sites.
How to Get Around EXIF Data
According to the FBI’s site, here are some of their suggestions. So, keep in mind that many people do know how to do this and are doing it.
- Turn off your phone or camera’s geo-location feature before ever taking the picture. Note: devices in airplane mode can still capture geo-location information.
- Remove EXIF data before sharing images with people or posting them online, especially when images are captured in private homes or businesses. There are free apps that you can use to do this.
- Use an EXIF viewer to verify that you were successful in stripping the personal data from the photos before sharing.
- Before uploading images, use available privacy settings to limit the audience to only your close friends and family.
- Minimize the use of apps that automatically upload and share captured images.
- Even without EXIF data, the image may contain identifying information, such as associated persons or location histories. Screen content with the assumption that anyone can see, copy, or forward photos that you post online.
Image Tip
To find an image’s exif data, right-click the photo and select either “properties” or “information”. If the GPS coordinates appear, simply type them into Google Maps to find the location.
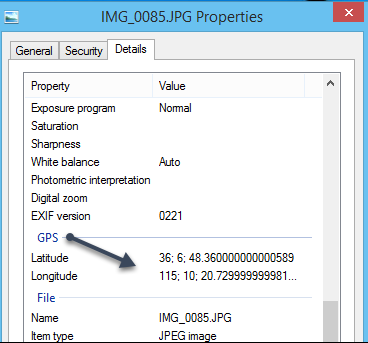
While this is a long shot, it is worth the effort should you find a photo online that was not shared in social media and appears to be recent.
In a recent blog post, we suggested trying Photo Investigator: The Photo Investigator is an iOS app to view all image metadata (all the possible data stored ABOUT and within each photo). You can also remove photo metadata with an in-app purchase. The Investigator can also open the image’s GPS location in the maps app for directions; view images at full size and zoom them larger than in the Photos App.


