I recently had an insightful conversation with a Paralegal on using social media for deposition cases. He shared with me that the firm he works for conducts social media research on everyone. He shared that it was the only way they knew if their clients were being truthful with them. Too many times they learned of mistruths during the actual deposition. Can you imagine? Social media intelligence is becoming increasingly necessary for many cases.
That led me to think about what we do when we conduct social media/deep web research on a person of interest for a client. The who, what, where and why is becoming more and more important. Let’s beak it down even further.
The Who- What – Where – & Why –
- Who: The who is the demographic information on your person of interest. This plays an important role in how we approach the search. Staying up to date on social media usage by demographics will help you narrow down your search a bit. Or, at the very least, give you a starting place.
- What: What is the case about? Is it fraud, infidelity, workman’s comp, insurance fraud? This matters a lot. Depending on the case, there are less obvious sites to take a look at. For example, if an employee is stealing merchandise from their place of employment you may need to visit eBay or Craigs List.
- Where: What area of the country does the person live? Someone living in a small town with limited resources may approach things differently that a person living in a huge city. The number of friends may be significantly larger in Facebook just because the city person may know more people.
- Why: The why has to do with what you are specifically looking for. “We need to know if the suspect was active in sports after a certain date.” We are given this information by our clients many times. By knowing this information, we are able to use our time better by looking in social media specifically for this type of posting.
Stay Up To Date With Statistics As Part of Your Social Intelligence Process
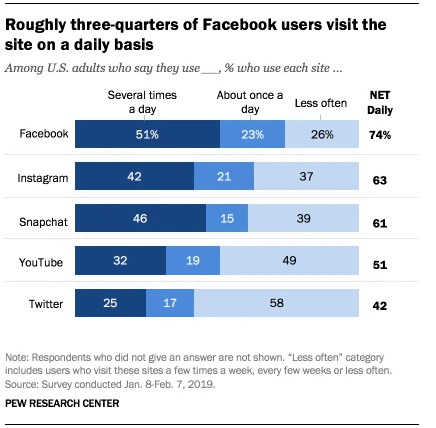
Researchers are trained to keep up with changes in social media usage. It is part of an overall social media intelligence strategy. And that is not an easy task because people change their usage all the time. Ask any social media marketer. They are constantly looking at what is new in each platform on a weekly basis to be sure they are hitting the right audience with their marketing.
You see, it is not only about software. Software helps us to pinpoint areas of interest and certainly gives us additional, important clues. It helps to streamline the process. However, the human side is just as important if not more. Artificial intelligence and the understanding of algorithms are important but they have in no way replaced skilled researchers.