Riots and Reddit are probably not something you would think have anything in common. However, because of the way Reddit is organized, it has been a resource for investigative journalism. It is heavily used for the monitoring of riots across the US.
Let’s start with the basis. What is Reddit, you may ask? Reddit is a large group of forums that discuss all kinds of topics of interest. The site explains itself as the “front page of the internet,” and that’s not an empty boast. Reddit is the sixth most popular site in the United States, according to Alexa, and the 18th worldwide.
Within Reddit are Subreddits. Subreddits are pretty much what they sound like, subgroups that are more specific in nature topic wise. Some of the subreddits are public, while others are private. They’re denoted by /r/, followed by the subreddit’s name, e.g., /r/gaming. The site has many “web sleuths” who use the power or crowdsourcing to reveal video footage of events all across the world.
Portland Subreddit Group
Portland, Oregon has a subreddit page that has 170,000 members and offers live streaming of events. r/Portland is the name of the subreddit. It contains lively conversation, Twitter resources that journalists are using to post about what is happening each night in their city and much more. It is one example of how a subreddit can be used within Reddit for riot monitoring.
Local Resident Uses Subreddit to Assist Police in Hit and Run
Here is a great example on the worth of understanding how Reddit works. One user posted an image of a piece of broken taillight, asking if anyone could identify the type of vehicle it came from. After 400 comments and some back and forth, it was identified correctly by make and model. The user was able to go to his local police station, place a report of a hit and run and provide the officer with the information. This helped aid the officer in finding the owner of the vehicle based on the proof.
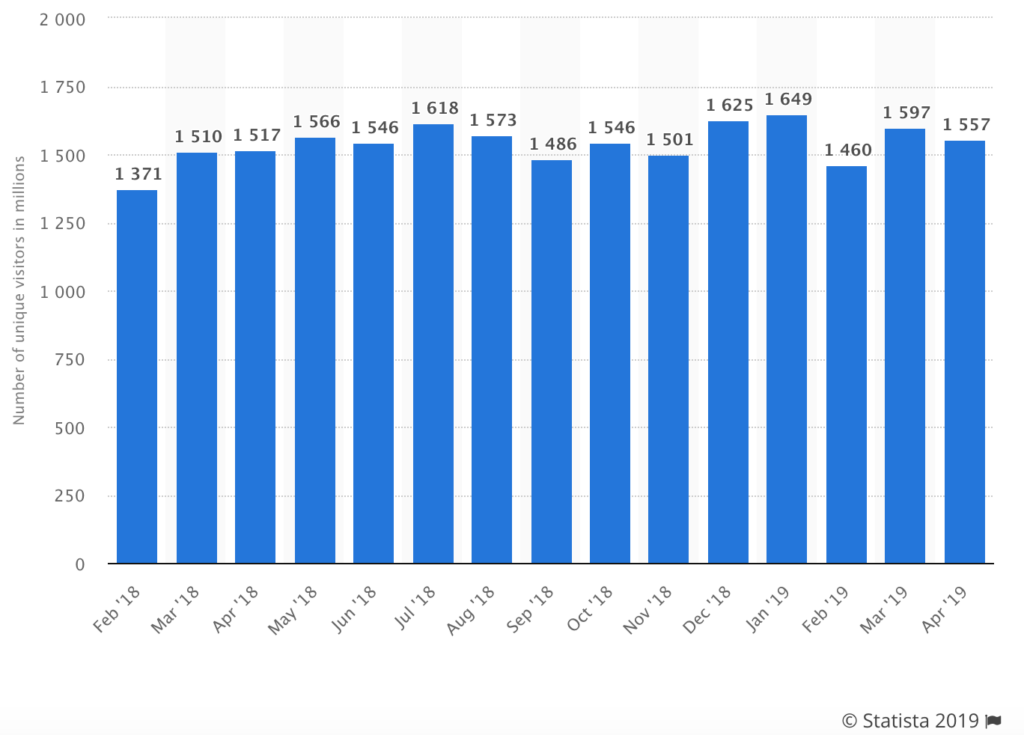
Reddit has grown its user base by 30% year-over-year, according to new data released by the company Wednesday. The self-proclaimed front page of the internet now reaches 430 million monthly active users, who collectively have created 199 million posts and 1.7 billion comments.Dec 4, 2019
source: Varitey.com
Interestingly enough, Reddit is an excellent resource for the Private Investigator or OSINT (open source intelligence) professional. In fact, I believe it is just as important as TikTok, Facebook, Instagram and LinkedIn. So, the next time you are ready to do your own online investigation, don’t forget to check Reddit!