For those unfamiliar with the term OSINT Research, it is explained this way by Wikipedia
Open Source Intelligence (OSINT) is the collection and analysis of information that is gathered from public, or open, sources.[2] OSINT is primarily used in national security, law enforcement, and business intelligence functions and is of value to analysts who use non-sensitive intelligence in answering classified, unclassified, or proprietary intelligence requirements across the previous intelligence disciplines.
OSINT sources can be divided up into six different categories of information flow
- Media, print newspapers, magazines, radio, and television from across and between countries.
- Internet, online publications, blogs, discussion groups, citizen media (i.e. – cell phone videos, and user created content), YouTube, and other social media websites (i.e. – Facebook, Twitter, Instagram, etc.). This source also outpaces a variety of other sources due to its timeliness and ease of access.
- Public Government Data, public government reports, budgets, hearings, telephone directories, press conferences, websites, and speeches. Although this source comes from an official source they are publicly accessible and may be used openly and freely.
- Professional and Academic Publications, information acquired from journals, conferences, symposia, academic papers, dissertations, and theses.
- Commercial Data, commercial imagery, financial and industrial assessments, and databases.
- Grey literature, technical reports, preprints, patents, working papers, business documents, unpublished works, and newsletters.
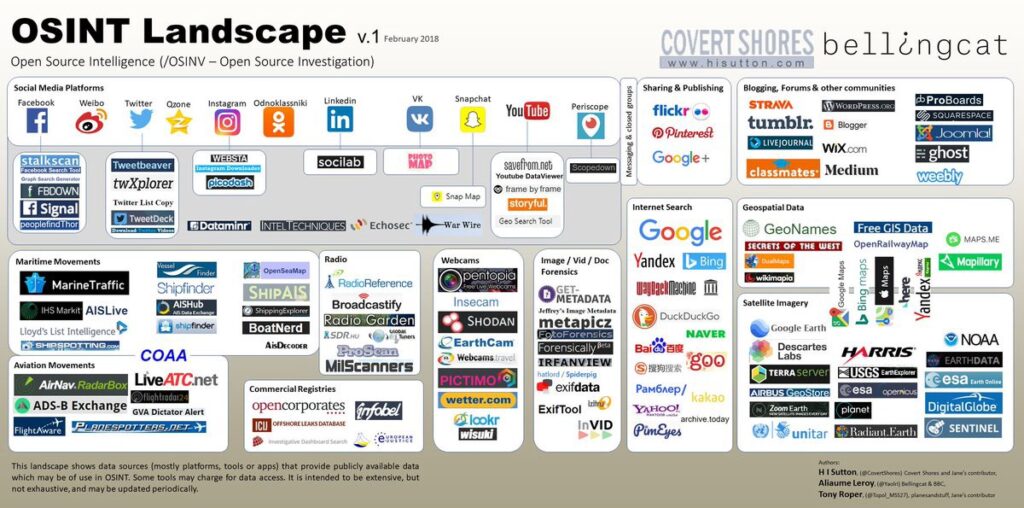
OSINT Resources Reveal the Details From the Deep Web
Many times our clients want to better understand the difference between a social media scan and a deep web scan. Taking a close look at the image above explains a lot and kind of surprises most people in terms of the data on the web that is openly available.
eChatter Case Study Examples of Deep Web Details
- Recently, we were trying to find out whether a POI (person of interest) was married. He had no Facebook clues other than he was in a relationship. After conducting a deep web scan we found a local newspaper article in which he was named along with “his wife”. The wife chose to keep her maiden name.
- A deep scan was ordered by a client to determine what happened to a deceased person’s body. We found an association letter that was published online indicating the person was cremated and buried at sea.
- A client needed to know if their POI had any business affiliations that wasn’t disclosed in a divorce settlement. After a deep scan was conducted, we located quite a few businesses tied to the POI.
Does it always work out this way? Not at all. Mainly because some people are much better at hiding this than others or because they were advised to delete everything online by advice of counsel. However, these are the kind of details OSINT research is all about. You will not find this in a Google search.