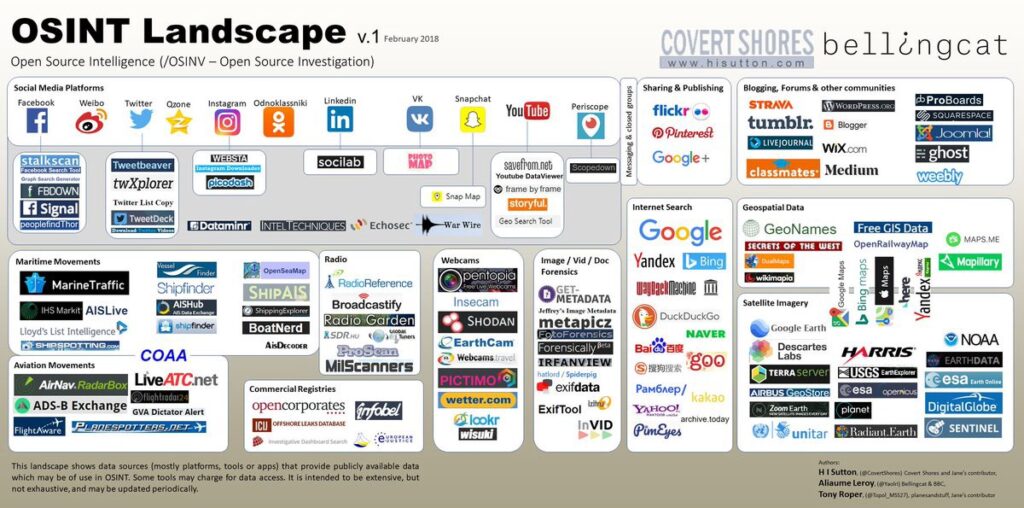
We have had a few requests over the years asking if there is a way to search an email address to see who it is tied to. There are actually numerous ways in which to do this on several different sites. Many of them require payment of some kind. You can try basic searches in Google, Bing and Yahoo first, however if you come up empty there, where do you go?
Interestingly enough, data breaches over the years have become an open source researchers’ best friend. In part this is due to the fact that when there is a large-scale data breach, it is often obligatory for the business to provide a site in which a user can check to see if they are part of the breach.
When searching for an email owner, we may want to know if the email is valid. Does it even exist or is it a made up, dummy email? By using some of the resources in this post, you can at least get confirmation that the email is valid. For example, if you discover the email has been part of a data breach, chances are it is a real email address. We can go one step further to say, with a degree of confidence, that it is most likely tied to other discoverable items in the deep web.
Not all data breach sites allow the user to look up another person’s email address. Most want to verify you are indeed the owner of the email address and genuinely want to know if your email has been compromised. There are a few that are not as strict. Two example sites that offer a quick and easy scan are:
Have I been Pnwed?
A quick search here will tell you if the email address has been part of a data breach or not. While it isn’t going to give you any details, it will give you a number of times it has been included in a breach of some kind.
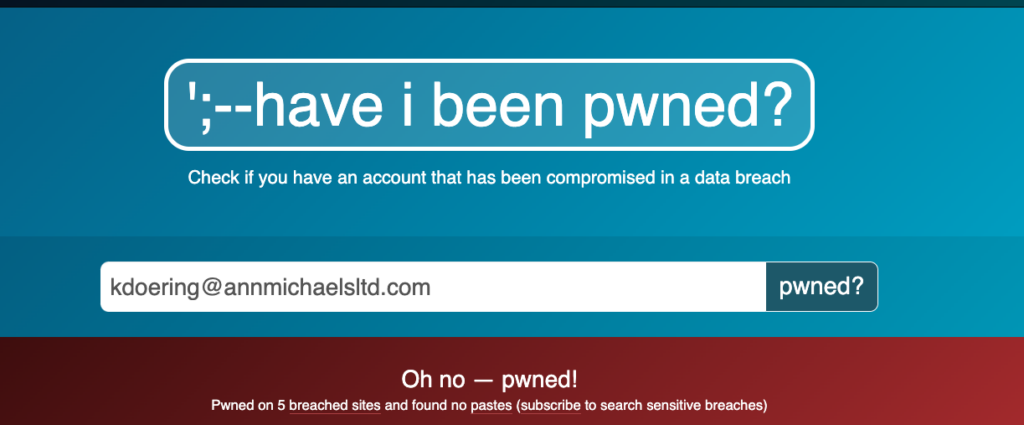
You can see that a quick scan of this email address indicates it has been a part of 5 breached sites but doesn’t tell you which ones. It does let you know that it is most likely a “real” email address.
Avast Email Check
Another site you can try is Avast. This is one of the newest sites that provides users the opportunities to scan for a “friend’s email address”.
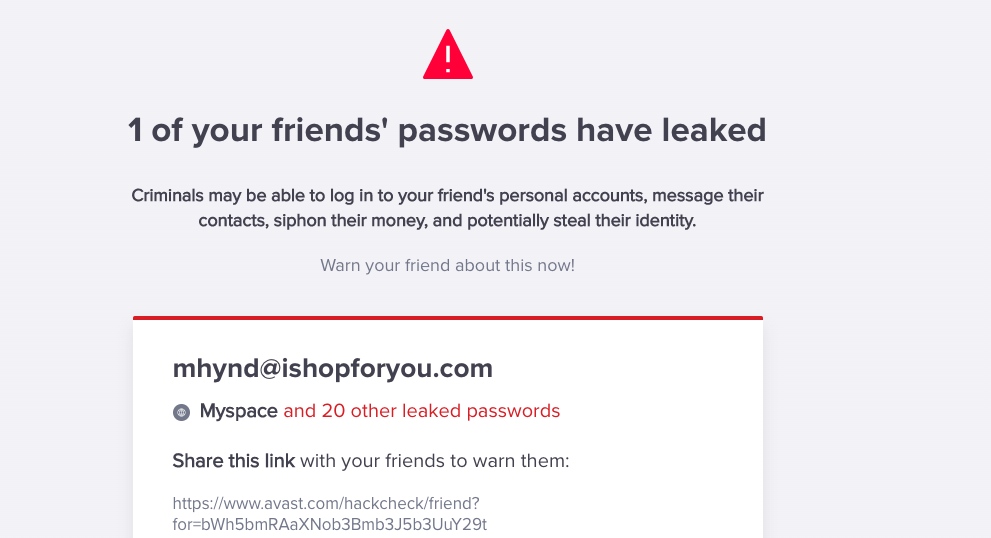
Marianne’s email was linked to MySpace, which leads me to think that she had an account at some point tied to this email address. I would search on the site to see if anything still exists in MySpace.
You may also want to try variations of the email address just in case you find closely configured email addresses. Use Google, Bing to search them to see what you come up with.