One thing we know for sure; cyber criminals attack corporate executives. The bigger the company, the higher the stakes. Mid-size companies may also be a target because those executives are time poor & money rich. It is exactly that space that I believe Investigators have their biggest opportunity to grow their business by offering this protection. You may have even had opportunity to conduct this research for a client or two in your own experience. But doing an OSINT sweep once a year may not be enough. I would suggest an ongoing program and will walk you through how to pitch this to your business clients.
Understanding the Treat
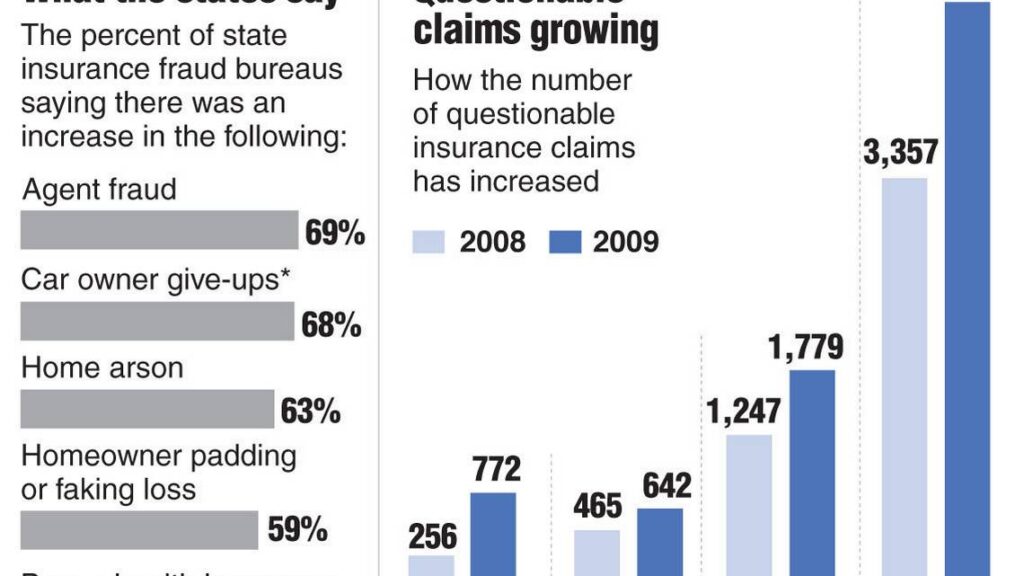
Price Waterhouse Cooper (PWC) ‘s recent report, “23rd Annual Global CEO Survey,” reveals that around 80% of CEOs have changed their online behavior due to potential risks. Corporate Espionage is alive and well and needs to be taken seriously as more and more employees overshare in social media. This allows for competitors to gain excellent insight into a vast array of information that would not otherwise be easily obtained. Banning employees from using social media at work has proven to be a nightmare and monitoring their social media internally has major privacy concerns. However, when approached correctly this type of monitoring is very valuable to any business regardless of their size.
The Challenge of Balance
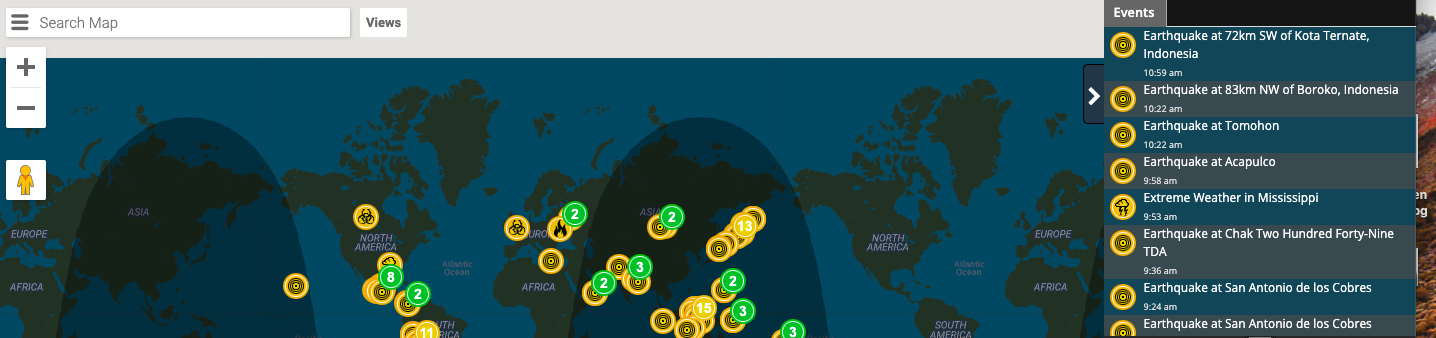
What makes this tricky, is that the company still has the responsibility to keep their employees safe, protect assets and data, mitigate risk for threats of fraud and monitoring reputation. High level executives travel to areas of the world that do not share the same security measures we do in the United States. All of this coupled with cyber security risks and you have a recipe for a potential disaster. In the photo below through the software we use, a Global Awareness search allows us to see natural disasters (i.e. earthquakes, fires, hurricanes,) as well as public security incidents’ in real time. A company’s HR team may wish to set a global awareness query around the area of travel and within the appropriate time frame. Real time alerts are set in place for immediate notification of potential risk.
In a nutshell, there are proactive steps that can be put in motion to ensure the safety of everyone.