When watching my local news the other evening, I heard of a case that really surprised me. A Town Commissioner of a small town in North Carolina, disagreed with his fellow board members over a specific topic. So much so, that he decided to create a fake Facebook profile and use it to harrass and argue with residents. Later, he admitted using a Charlotte area businessman’s real name & real profile picture. The surprising part of this is that we expect this from scammers, but not someone who would be sitting on a board of a city or town. It seems that these days, anything is possible. Being proactive is a must.
Online Impersonation Tricks
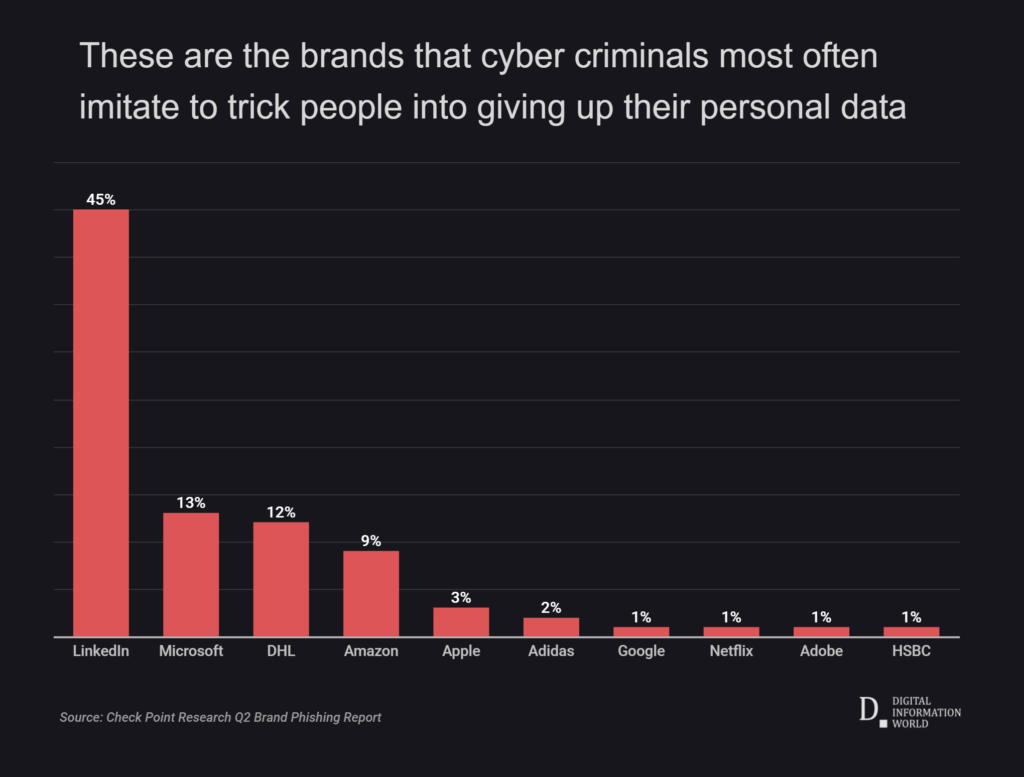
- Facebook Marketplace: Fake ads on the site have become a real problem. Some of the ads look like they are from legitimate businesses such as Home Depot, Lowes, etc.. They make the post look very real, using lots of pictures. The Better Business Bureau says the fake ads are common and they get thousands of complaints each year. “Impersonation is one of the key factors of what scammers love to do,” Sarah Wetzel of the BBB said. “They love to impersonate those well-known companies because that way they already have a foot in the door with the consumers.”
2. Rental Scams: Scammers ( who operate anywhere in the world ) can advertise a fake rental online. Next, they add a sense of urgency to attempt to get a deposit on the property. They will use excuses as to why they can not meet you in person. They also make sure to tell you that several people are looking at the property. Nationally, over 230 rental scams have been reported this year, up from the same time last year. Victims report losing an average of $550.
Better Business Bureau offers these tips:
- Do an online search for the landlord’s email and phone number. If the same ad is listed in other cities, that’s a red flag.
- If you can’t see the property in person, try to find someone you trust to go and confirm the unit is what’s being advertised online.
- Don’t fall for deals that are too good to be true. If a unit is well below market rate or promising extra amenities than normal, it could be a red flag.
- Be wary of required payments through cash transfer apps. Peer to peer apps are meant to be used with people you know.
Use the Better Business Bureau’s scam tracker as a tool to both report and prevent scam.
3. Catfishing: When someone creates a fake identity online for the purpose of starting a relationship. They then use this as a way to gain interest and confidence so they can scam the person out of money. Social Catfish is a software company that works to help people who believe they have been the victim of catfishing. It is one of the many software platforms we use at eChatter when conducting online research. They also have a great reverse image tool within the platform.
Impersonation of a Business
This is sometimes called Domain Spoofing. When done correctly, it can damage a business’ reputation while scamming consumers who fall for their pitch. All while impersonating the business. Two of the most common ways is cybersquatting and typosquatting.
- Cybersquatting: Scammers use already established business websites and copy them to look just like the real website. They then sell counterfeit products.
- Typosquatting: Scammers register a domain name similar to that of the legitimate business. They purposely use typo errors to change it but at first glance, people take it as the legitimate company’s website. This is sometimes used to redirect someone to a competitor’s website or try to collect ad revenue.
This just scratches the surface of the many ways scammers use the web and social media. It is a subject we will continue to write about in the future, so check back often for updates.