Many criminals continue to turn to the internet to unload stolen goods. Some sites require more information than a thief is willing to part with, which then leads them to other sites that have less security. Because of the anonymity some sites offer, it is important to search for the type of goods being offered on the site. User name searches are not always fruitful. Searching for items may back you in, if you will, to the criminal’s information.
Equally important is the rise of employee fraud. We wrote about this earlier this year. In Employee Fraud in the Digital Age, we discussed a case study. We once worked on a scan for an Investigator whose subject was suspected of selling a very unique set of stolen auto parts. The employee had created an eBay account and made the mistake of using a familiar user name. After the user name was revealed in our Deep Web Scan, we turned our attention to the online websites that sell goods to consumers. We were able to piece this information to that of our client’s subject. A huge catalog of stolen auto parts were on display.
Online Sales
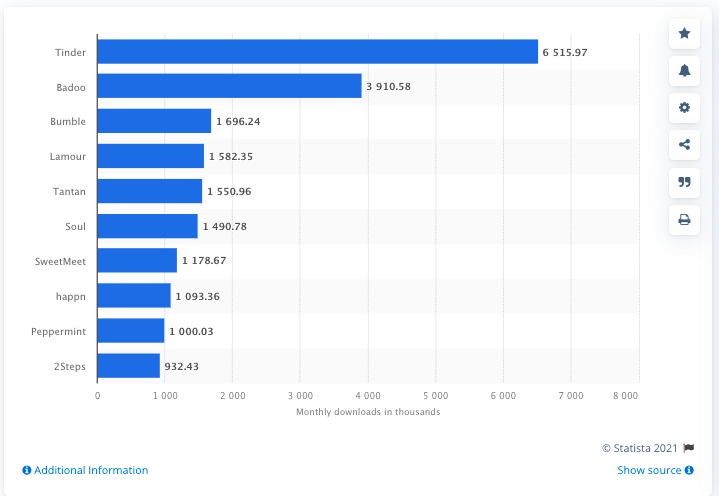
According to Web Retailer, “47% of ecommerce sales were made through online marketplaces in 2020, amounting to nearly two trillion dollars. They also list 155 marketplaces that have more than one million visits per month, internationally.
How did this explosion in online selling happen? Over time it evolved, of course, but within the last couple of years, more and more people rely on it due to the Pandemic. Each online platform works differently, making it very difficult to find the scammers. Let’s take a look at a few of the top marketplaces to start.
Facebook Marketplace
Facebook noticed that its users were buying and selling things in groups across the platform. In 2016, it created a dedicated hub where people could post items for sale in order to reach interested buyers. They created what is now known as Facebook Marketplace, and they grew it to 1 Billion users.
The volume alone dictates that it will be a breading ground for fraud and scammers. Facebook is well aware of the issues they have and have publicly stated that they use software as well as outsourced people to review listings flagged by the software and to answer user complaints.
Most recently, you can find fake COVID vaccine cards for sale. However, for the most part you can find just about anything here.
Amazon Online Sales
It is a little more difficult to sell on Amazon. You can either sell your products to Amazon or on Amazon.
As a consumer, it is important to pay attention to who is selling an item. For example I recently purchased a specific style of shoes. I didn’t think much about it and when it was delivered it was an obvious counterfeit. It even had a very strong chemical smell. It was obvious I was a victim of a seller of counterfeit goods.
The Washington Post recently had a great article titled, “How to tell real products from scams when shopping online.” They actually listed out some good OSINT research tips, such as doing a reverse image search on the item you are looking at. It is also smart to research the company name.
eBay Online Sales
When it comes to online sales fraud, you most likely think eBay. eBay has been around since 1995 and it is no stranger to these issues. While there are many other marketplaces, It is still a gigantic places to sell all kinds of used and new products. When conducting research on a person or company allegedly selling stolen goods online, it is still the best place to start.
A couple of OSINT tips when searching eBay:
- Search the site for every known user name. You may even want to mix it up a bit by mixing user name letters and numbers. For example, consider the following fictitious user names; @windycity146, @tom.day, @daytom – I would search each of these but then combine to create new ones that the user may be using on eBay. Such as @tom146, @day146, etc..
- Search the site by utilizing the “Advanced” button, which will display new options for searches. Toggle to “show results” and then “items near me”. From here you can plug in a zip code up to 10 miles or more. This is an excellent way to search if you do not know the user name of your suspect.