Social media in many ways is still the wild, wild west. It is a lawless environment in which many people have been harmed by reckless comments. Over the last year, we have seen several cases in which one person was harassing another person in social media.
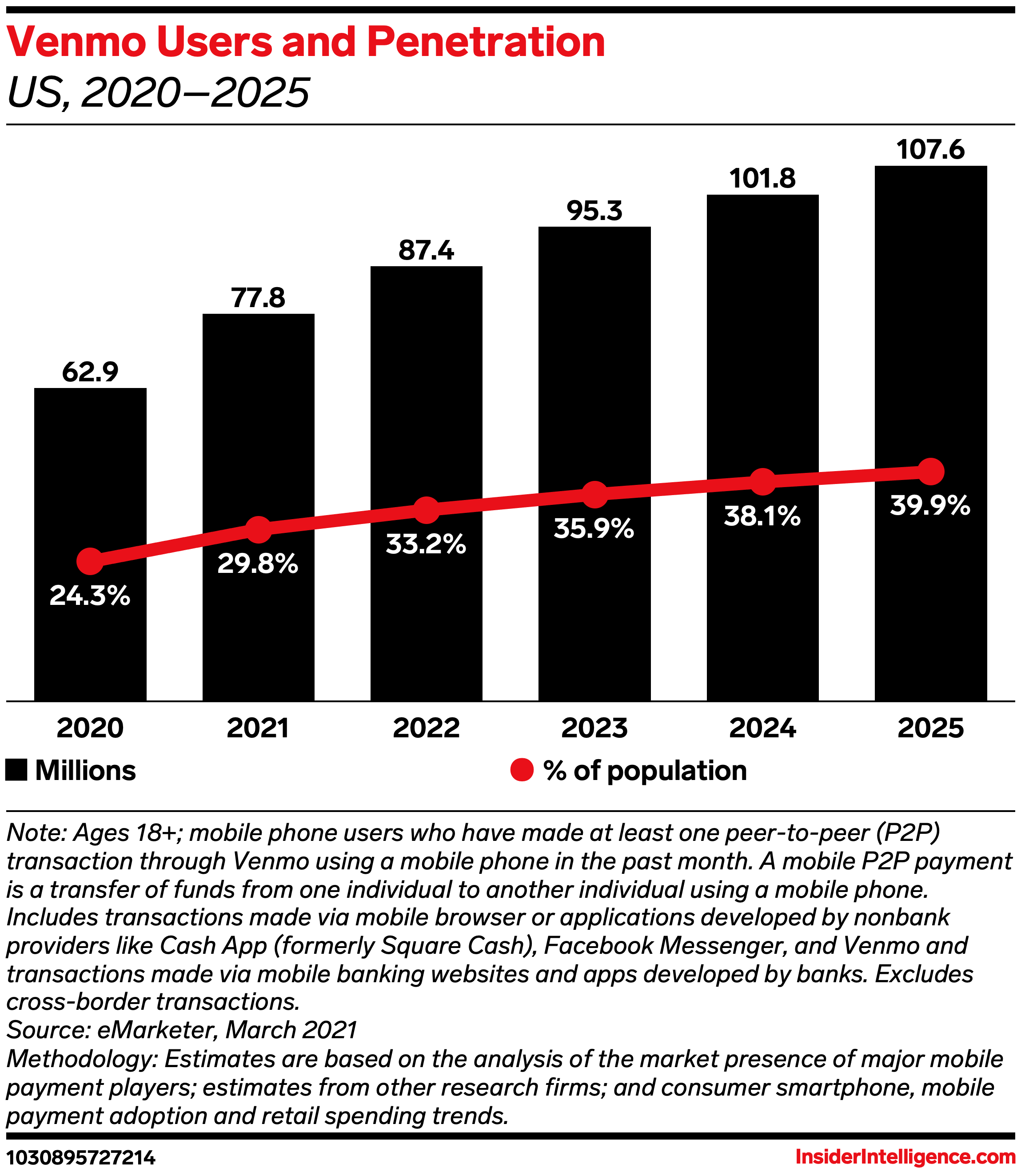
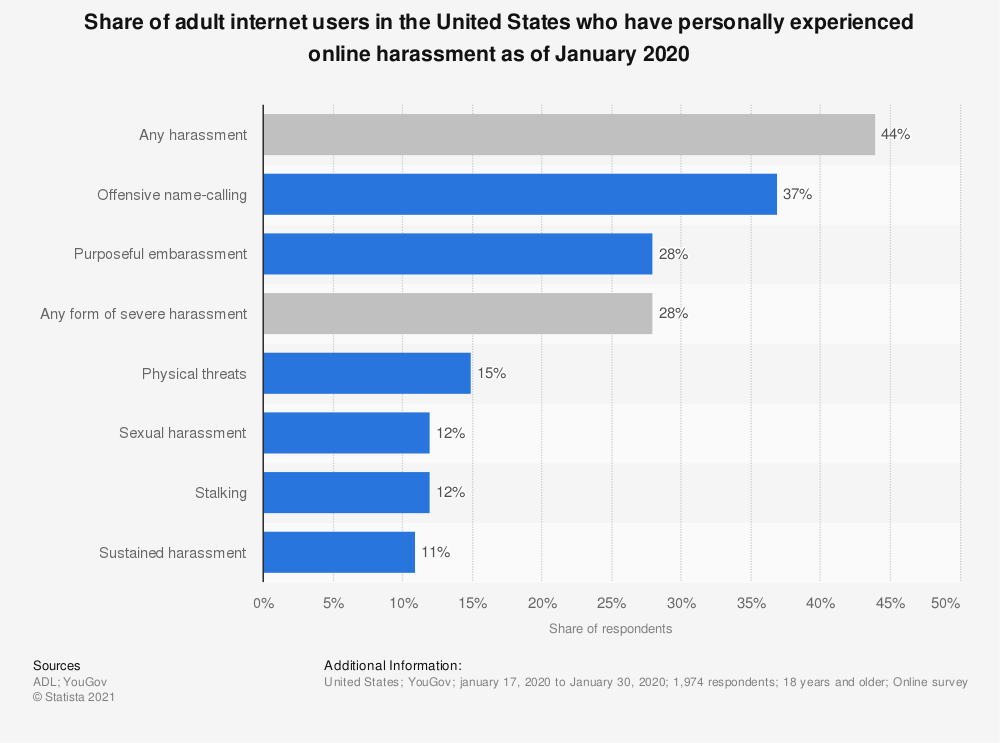
How common is online harassment? During a January 2020 survey it was found that 44 percent of internet users had personally experienced any kind of online harassment with 28 percent of respondents reporting to having experienced severe forms of online harassment such as physical threats, sexual harassment, stalking and sustained harassment.
What is Considered Defamation?
According to the Electronic Frontier Foundation (which has a great web page on online defamation law), there are three elements that must be shown during a defamation claim:
- The statement has to be false
- It has to be communicated (published) to someone other than the person being defamed
- It has to be about the plaintiff and have the potential to harm their reputation
Written defamation is considered to be libel. Verbal defamation is considered to be slander.
For a statement to meet the legal definition of defamation, it has to be a false statement by a third party. Additionally, it needs to be intended to do serious harm to a person’s reputation. It has to be done “without fault”. You must be able to show someone was acting irresponsibly when making the statement.
Examples of Social Media Defamation
HG.org legal resources outlines social media defamation examples as follows. “Not every untrue or unkind statement is actionable. However, many statements are. For example, if you accused a person on social media of abusing his or her spouse or children, such a statement would likely be considered defamatory if it were not true. Even if an individual posts information that is partially true and partially false, he or she can be found liable for defamation. For example, a person may claim that an individual was fired for harassment. The individual may have been fired but not for harassment. The court may find defamation still existed despite some truth to the statement.“
Steps to Dealing with Social Media Defamation
Most businesses are monitoring online content through social media and the web. Most individuals are not. You may not even be aware of someone posting negative information unless an associate tells you about it. On the other hand, you may be very aware because the person has set out to harrass you online.
- Do not respond. This is hard to do. Responding hastily can just make the situation worse.
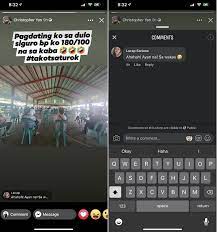
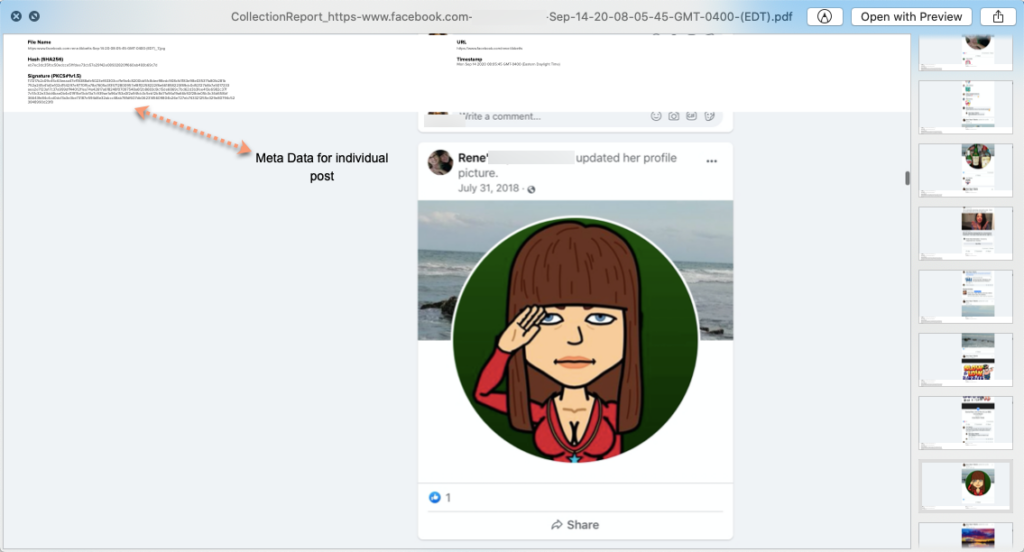
- Capture the evidence. Take screenshots as soon as you can in order to collect the posts. This will at least provide you with a good point of reference if things get worse.
- The next step is to either hire a Private Investigator or an Attorney. Getting legal help is very important if it doesn’t look like this is going away. Either will be able to conduct some research on the perpetrator. You may not be the only one this is happening to. Legal help will also be able to authenticate the online evidence should it go to court at any point in time. An Attorney may be able to provide you with a Cease and Desist Letter.
- Notify the social media company. Check out the resource pages. You may be able to report this.
Always be careful. This is especially true if the person lives near you. Exercise caution until you get it resolved.