Instagram is one of the most popular photo sharing apps to date. Allowing users to take selfies, discover new filters, talk about themselves, and so much more. Poparazzi flips the script of Instagram and allows users to ONLY share photos of their friends. No selfies allowed! Poparrazzi intentionally takes away the front-facing camera feature so users can only capture photos of their friends and tag them. Poparazzi simply put, mimics a Paparazzi shot.
“We built Poparazzi to take away the pressure to be perfect,” the company wrote in a Medium post announcing it’s launch. “We did this by not allowing you to post photos of yourself, putting the emphasis where it should’ve been all along: on the people you’re with. On Popparazzi, you are your friend’s paparazzi, and they are yours.”
Why So Popular?
In a selfie crazed culture, why is taking pictures of friends all the hype? Believe it or not, there’s been a significant demand for a less performative social platform- mainly among young users. Gen Z is becoming known for their actions, taking the focus off of oneself, statements, or promises made online. They are a leading the way as one of the most impact driven generations to date. Focusing on others over oneself.
According to a recent USA Today article, Youth interest in civic engagement is soaring among the generation that the global volunteering nonprofit Points of Light says was already the most active in history. More than half (53%) of Generation Z individuals said they wanted to get more involved in their communities post-COVID, which was higher than any other generation, according to a 2020 Points of Light survey. (Gen Z includes those born beginning in 1997, so they’re 24 and younger.)
There are several other startups that listened to the voice of young users, like Gen Z, and created similar apps like Poparazzi. These include Minutiae, Vero, Dayflash, Oggl, Dispo, and Herd.
How To Use Poparazzi
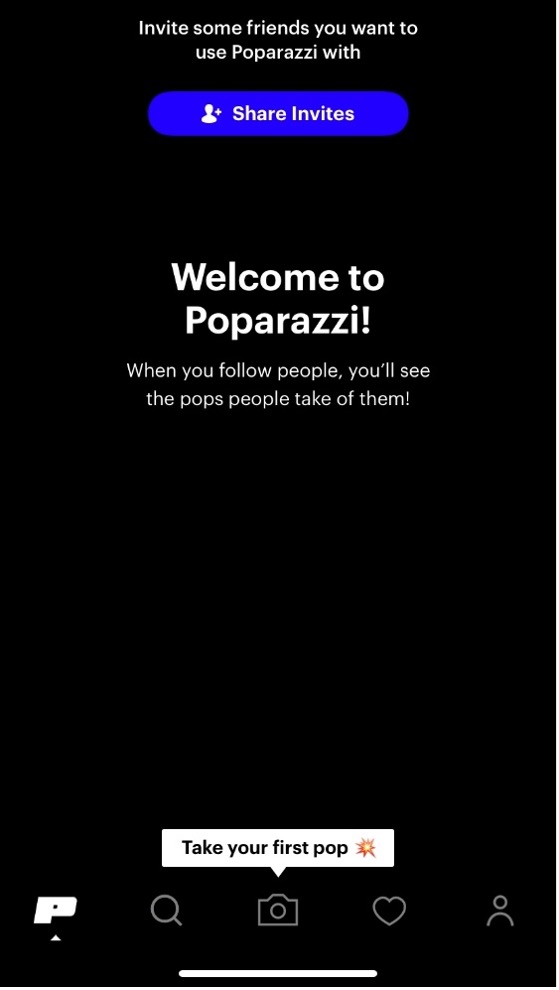
One you download and launch the app, a video advertisement is shown, “Your friends are your paparazzi, and you are theirs.” Several photos are shown of teens together with their friends, at parties, football games, in college, and hanging out in groups. After you press “Get Started” permissions are asked since Poparazzi is a photo sharing app. You must allow Poparazzi to access your camera, contacts, and notifications to begin. It then asks you for your age, phone number, name, the username you want to use. Anyone from your contacts that has the app is then shown, inviting you to start following people. Once you have created your account the app takes you to the home screen, motioning you to take your first “pop” which references taking your first picture. Other buttons include search, activity, and your profile.
Mobicip explains, “The most important feature of Poparazzi is that is does not allow users to crop, add captions, filters or any edits to the photos taken. People may be tagged on photos, but they must be on your follow list for the tagged photos to appear in your account. The app automatically follows everyone in the phone book of the phone into which it is downloaded. A “pop” score is given to each profile depending on the number of photos taken. Users also have the option of deleting and untagging pictures they do not want on their profile. Other users may be blocked to prevent “popping” pictures of them and prevent them from tagging your name.”
Other current features are the ability to share a public pop to Snapchat, Instagram Photos, and Instagram Stories.
Searching Poparazzi
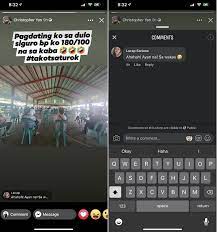
Using the small magnifying glass icon on the bottom of the app allows anyone to search through the platform. “Featured Pops” (public pictures taken) flood the screen of young user photos. Some in high school, others in college. These are all public profiles of people, just like you would potentially see on Instagram or TikTok when searching. You can publicly search usernames through the app or follow anyone who has a public account. For investigative purposes, this is another app that is worth downloading, learning, and understanding. Especially if you have any cases with individuals 24 years old or younger. You can easily search for anyone in your contacts, but also usernames, and names of individuals. Remember although others are taking photos of someone, those photos are then tagged and shown on that individual’s profile.
The Dangers
There are several dangers to the platform, like there are with any social media app available. Immediately as I searched the profile, I came across photos of a student pretending to cut another students head off with a real axe in a classroom setting. The next set of photos shown was of a car crash involving two teenage girls. Another of a girl using the restroom in a bathroom stall. Her friend popped over the top of the stall and took her picture. My initial thought when scrolling through? There is a huge lack of privacy within this app but for others who could maliciously post photos of other people.
There are several articles sounding the alarm to the dangers of this app. One interviewing Dr. Pamela Wisniewski, a professor at the University of Florida, who studies the impacts social media has on people.
“Somebody’s going around taking pictures and sharing it of them without their consent,” said Wisniewski. “While there could be some fun and beneficial ways to use an app like this, as you can imagine, there’s also some ways to use it in malicious ways that can actually harm people’s reputation, share embarrassing or potentially harmful material about somebody that then is on the internet to stay.”
Wisniewski adds that it could be tough for parents to take down photos that they do not want posted of their kids. “Being able to wrangle in that content especially once it’s been shared is almost impossible to do,” she said.